You might not be aware of this, but October is actually a very significant month for us in the IT community. No, not because of Halloween, or even Thanksgiving, but for something else – October is Cybersecurity Awareness Month!
Considering this special occasion, we thought we’d take the time to speak on a topic that’s very important to essentially anyone with a computer: email security. Email is one of the top communication tools used in businesses but is also one of the most vulnerable. Sophisticated phishing attacks account for more than 80% of reported cyber security incidents and lead to an estimated loss of $17,700 every minute. While phishing attacks is the main tool used by cyber-attackers, robust email security also demands protection against spam, viruses, theft of passwords, and ransomware. In this post – we’ll detail some quick and easy tips that can help keep your email inbox and your information more secure.
The Red Flags of Phishing Attacks
While email phishing schemes are likely the most well-known threat to your inbox; they are still the most prevalent and the most likely cyberattack you’re likely to encounter. The most prolific weapon you can have in your arsenal to protect you against phishing attacks is knowing how to recognize them. Common examples of phishing scams include offering a coupon for a free item, saying your account is on hold and you must make a payment, asking you to confirm any personal information or warning you that there is suspicious activity on your account, etc. These examples are note, however, exhaustive, but they should raise immediate red flags.
The Look of a Suspicious Email
Aside from the major red flags mentioned above, cybercriminals often leave other clues to warn us away. Here are some of the typical ones:
- Typos: Large, legitimate corporations typically have their emails vetted and proofread. A significant amount of typos or poor command of language is an easy clue to spot that should give you pause.
- Strange URLs: scammers sometimes insert phony URLs into their phishing emails to make them seem properly connected to the organization they are pretending to represent. However, if you hover over the URL (without clicking on it!) you can usually confirm whether it is real or not.
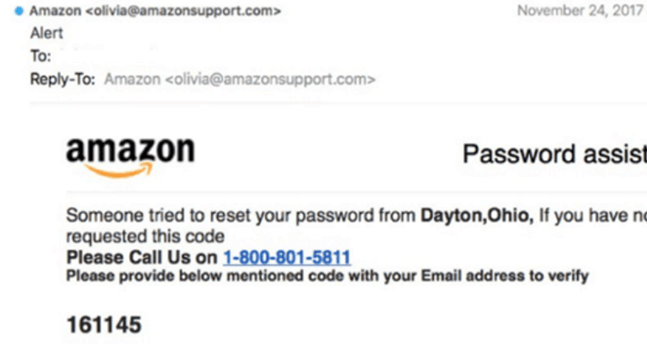
Additional Clues:
- Sender’s email address doesn’t match the company
- Multiple requests to click on a link
- Poor layout/formatting
- Requests for personal information
Keeping Your Inbox Secure
Aside from recognizing dodgy emails, there are other general tactics you can use to keep your inbox secure overall.
Firstly, it’s time to ditch the password you’ve had since middle school. Even though it’s widespread knowledge that strong password use is essential, bad password practices are still rampant. A recent poll showed that 91% of people knew that using the same password for multiple accounts was a security risk but did it anyways most or all of the time. Strong passwords should avoid obvious words or phrases; essentially the more random the better. There is a term called a passphrase which is recommended, which involves combining multiple, random words into a string of at least 15 characters. Aside from creating a strong password, make sure not to share it or save it somewhere easily accessible and if you feel it’s been compromised change it immediately.
You can also turn to tech solutions to help keep your emails secure. To start you should install a reliable antivirus software. This will help you be protected from many viruses, spyware, malware, and other online threats. If you want to take your technical security to another level, you can look into installing an inscription software for your emails. Especially if you are often sending sensitive information or materials via email there is a certain amount of risk that comes with that. This is because most emails are submitted in plain text and is not well protected as it travels between you and who you’re sending it to. Both antivirus and encryption software are readily available to purchase for both personal and business use.
Back It Up
It’s advisable in the instance that you are the victim of a successful cyberattack to have a backup. Most prominent email providers have a built-in archiving system that you can take advantage of or add on. These create an automatic backup of all email communication, which helps keep your email secure in the event of outside interference.




